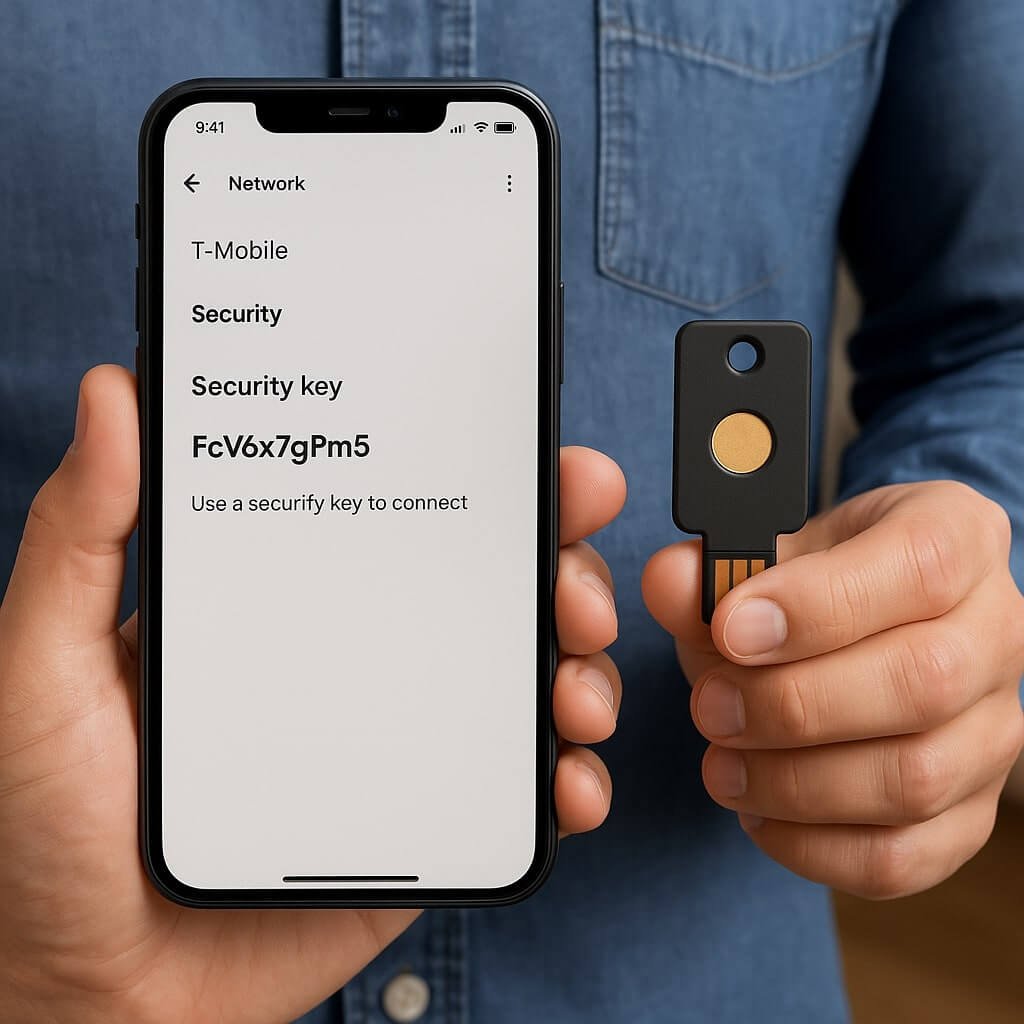
Understanding the T-Mobile Network Security Key is essential for anyone looking to protect their online presence. This key acts as a gatekeeper, utilizing advanced encryption techniques to shield your data from potential threats. It not only authenticates users but also guarantees that only authorized devices can access your network. As cyber threats evolve, so does the need for robust security measures. But what specific advantages does the T-Mobile Network Security Key offer you?
Key Takeaways
- The T-Mobile Network Security Key ensures a secure connection by implementing robust encryption standards to protect data from cyber threats.
- It verifies user identity through unique authentication methods, allowing only authorized devices to access the network.
- Regular updates to the security key enhance defenses against evolving cyber threats, minimizing risks of hacking and data breaches.
- The key aids in maintaining online privacy and prevents unauthorized access, making it essential for secure communication.
- T-Mobile’s commitment to security includes adapting to new challenges and integrating advanced technologies for user protection.
Understanding the T-Mobile Network Security Key
The T-Mobile Network Security Key is a crucial component for ensuring the safety and integrity of your network connection. By implementing robust encryption standards, this key safeguards your data from unauthorized access and potential threats.
When you connect to the T-Mobile network, the security key encrypts your information, making it nearly impossible for cybercriminals to intercept or manipulate it. You’re fundamentally creating a secure tunnel for your data, which bolsters overall network safety.
Understanding how to use and manage this key effectively is essential for maintaining your connection’s security. Regularly updating your security key not only adheres to best practices but also enhances your defense against evolving cyber threats, ensuring your network remains resilient and secure.
How the Security Key Works
To understand how the T-Mobile Security Key works, you need to examine its authentication process, which verifies user identity using unique credentials.
You’ll also discover the various key generation methods employed to create secure access codes.
This exploration highlights the security benefits that enhance your network protection against unauthorized access.
Authentication Process Explained
Understanding how the T-Mobile Network Security Key functions is essential for guaranteeing a secure connection. The authentication process relies on robust authentication methods and security protocols to validate your identity. When you enter the security key, it triggers a sequence where your device communicates with T-Mobile’s servers, verifying credentials and establishing a secure session.
| Authentication Method | Security Protocol | Description |
|---|---|---|
| Password | WPA2 | Uses a pre-shared key for access |
| Biometric | EAP-TLS | Employs certificates for validation |
| Token-based | RADIUS | Relies on dynamic tokens for access |
| Multi-factor | OAuth | Combines multiple verification layers |
| SMS-based | SIM Authentication | Confirms identity via SMS codes |
This process guarantees that only authorized devices access the network.
Key Generation Methods
While many users may not realize it, the process of generating a T-Mobile Network Security Key involves complex cryptographic algorithms and randomization techniques to guarantee uniqueness and security. The key algorithms employed assure that every generated key is distinct, minimizing the risk of duplication or unauthorized access.
Using a combination of pseudorandom number generators and hashing functions, T-Mobile creates keys that are difficult to predict or replicate.
Once generated, the key distribution process securely transmits these keys to your device, making certain they’re only accessible to authorized users.
This careful orchestration of algorithms and distribution methods safeguards your connection, making it critical to understand how these behind-the-scenes processes work to enhance your network security.
Security Benefits Overview
The T-Mobile Network Security Key greatly enhances your network’s safety by employing advanced encryption methods that protect data integrity and confidentiality during transmission.
By utilizing robust security protocols, it guarantees that unauthorized access is minimized and your sensitive information remains secure. Here’s how it works:
- Data Encryption: All transmitted data is encrypted, making it unreadable to unauthorized users.
- Access Control: The key restricts network access to authorized devices only, preventing potential breaches.
- Real-Time Monitoring: Continuous monitoring identifies and mitigates threats as they arise.
- Regular Updates: Security protocols are frequently updated, guaranteeing protection against emerging vulnerabilities.
These features collectively fortify your network, providing peace of mind as you navigate the digital landscape.
Benefits of Using the T-Mobile Network Security Key
Utilizing the T-Mobile Network Security Key greatly enhances your online safety and privacy. One of the key T-Mobile advantages is the robust encryption it provides, protecting your data from unauthorized access. This security enhancement not only safeguards sensitive information but also boosts your confidence while browsing.
By requiring a unique key for network access, you minimize the risk of cyber threats such as hacking and data breaches. Additionally, the T-Mobile Network Security Key allows for easy management of connected devices, enabling you to monitor which devices access your network. This level of control is vital in maintaining a secure online environment.
Setting Up Your T-Mobile Network Security Key
To set up your T-Mobile Network Security Key, you’ll first need to access your T-Mobile account through their website or app.
Once logged in, you can generate your unique security key, which is essential for securing your network.
After obtaining the key, you can use it to enhance your connection’s security and manage access effectively.
Accessing T-Mobile Account
How can you efficiently set up your T-Mobile Network Security Key?
First, you’ll need to access your T-Mobile account. Follow these steps to streamline the process:
- Log in to your T-Mobile account management portal using your credentials.
- Navigate to the security settings section, where you’ll find options related to account recovery options.
- Choose the setup option for your Network Security Key; this is essential for protecting your account.
- Follow the prompts, ensuring you record your key securely for future access.
Generating Your Key
After accessing your T-Mobile account, the next step involves generating your Network Security Key, an essential element in enhancing your account’s security.
To initiate this process, you’ll need to apply key generation techniques that guarantee the key’s strength and uniqueness. T-Mobile typically provides a user-friendly interface for this; follow the prompts to create a complex key, combining letters, numbers, and symbols.
It’s imperative to store this key securely, adhering to key management practices that minimize unauthorized access. Consider using a password manager for this purpose.
Using the Key
Once you’ve generated your Network Security Key, you can easily set it up to enhance your T-Mobile account’s security.
Proper key management is essential for protecting your sensitive information. Here’s how to configure it effectively:
- Log into your T-Mobile account – Use your username and password to access your account settings.
- Navigate to Security Settings – Find the section dedicated to security features and select the option for Network Security Key.
- Input the generated key – Enter the key you created previously to link it with your account.
- Save changes – Confirm you save your settings to activate the added security measure.
Common Issues and Troubleshooting
Many users encounter various challenges when managing their T-Mobile Network Security Key, which can lead to frustration and connectivity issues.
Common problems include incorrect key entry, network settings misconfiguration, and outdated firmware. When troubleshooting connectivity, double-check the security key for accuracy, as even a single character mistake can block access.
If you’re facing persistent issues, resetting your network settings might help. Additionally, verify your device’s software is up to date, as this can resolve access issues related to compatibility.
If you’re still having trouble, consider contacting T-Mobile support for further assistance. They can provide tailored solutions and help you navigate any persistent concerns you may have with your Network Security Key.
Enhancing Your Overall Online Security
While managing your T-Mobile Network Security Key is essential for maintaining a stable connection, enhancing your overall online security requires a more thorough approach.
To truly safeguard your online privacy and guarantee secure browsing, consider implementing the following strategies:
- Use a VPN: This encrypts your internet connection, masking your IP address and enhancing privacy.
- Enable Two-Factor Authentication: Adding an extra layer of security helps protect your accounts from unauthorized access.
- Regularly Update Software: Ensure your devices and applications are up to date to protect against vulnerabilities.
- Practice Caution with Public Wi-Fi: Avoid accessing sensitive information on unsecured networks to minimize risk.
Future of Network Security With T-Mobile
As technology evolves, T-Mobile is at the forefront of redefining network security to address emerging threats and enhance user safety. The company’s commitment to future innovations drives solutions tailored to tackle evolving security challenges.
| Future Innovations | Security Challenges |
|---|---|
| AI-driven threat detection | Increasing cyberattacks |
| Enhanced encryption | Data privacy concerns |
| 5G network security | IoT vulnerabilities |
| User education programs | Phishing and scams |
You’ll benefit from T-Mobile’s proactive approach, which not only anticipates potential risks but also equips you with robust tools. By integrating advanced technologies, T-Mobile guarantees that your network experience remains secure, allowing you to focus on what matters most without compromising safety.
Conclusion
In summary, utilizing the T-Mobile Network Security Key greatly enhances your network’s security posture. By employing advanced encryption and authentication measures, it safeguards your sensitive data against potential cyber threats. Proper setup and troubleshooting can further optimize your experience, ensuring seamless connectivity. As the digital landscape evolves, staying ahead of security challenges becomes vital. By integrating the T-Mobile Network Security Key into your network strategy, you’re taking a proactive step towards a more secure online environment.